How to install Backdoor on Router
How to Install a Hidden Backdoor in a Home Router
How to Install a Hidden Backdoor in a Home Router
In this short tutorial I will show you the basic concepts on how to install your own software in a home router. It can be a backdoor but it can also be a special monitoring tool or service. We will made some assumptions to keep this tutorial short and simple.- You have access to the router's control panel. This is the case when you own your router and you are practising your security skills on your own network.
- The router is running some Open Firmware. In this tutorial I'm assuming it is running DD-wrt.
Step 1: Enable Ssh Access
You can find out how to do that in the official page. Basically you have to click a couple of radio buttons, or type some commands on the command-line.ssh access will be required to copy our SW in the router and also to launch it.
Step 2: Get Information About the Architecture
As you are using your own router you already know that, but just in case these are some tips.- Log in the router using ssh (you had just enable it)
- In the command-line type uname -m. This command will tell you the type of processor installed in your router. It will probably be a MIPS SoC
- Also type cat /proc/cpuinfo to get further details.
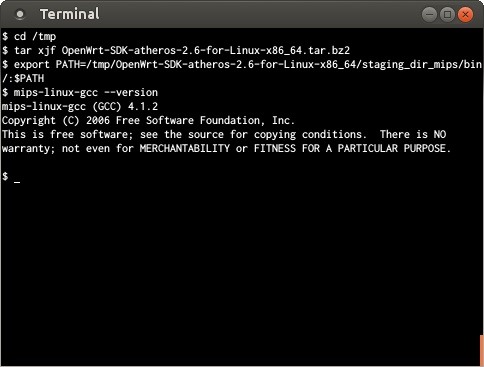
Step 3: Get the Appropriated Toolchain
Now you need to get (or build) a toolchain for your router platform. In my case I just got one of the official DD-WRT toolchains for MIPS. I'd got the information from one of the messages in the dd-wrt forums.Download the toolchain and install it.
Step 4: Installing the Toolchain
In general, you just need to do two things to install a toolchain.- Uncompress the toolchain package somewhere in your disk
- Add to the PATH the directory with all the toolchain binaries.
For the specific toolchain I am using it is actually mips-linux-. That's important if you have to cross-compile autotools packages... but we are not going to talk about this here.
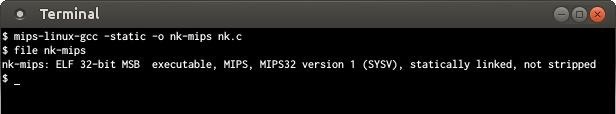
Step 5: Compiling
To keep this tutorial simple, I'm going to use, once again, Netkitty. This tool is pretty convenient because it does not rely on any external library and therefore, we can just compile it. I'm not covering in this tutorial how to compile other tools that requires libraries. You can found a lot of information on the Internet about cross-compiling and staging packages, in case you need to do that.To compile NetKitty we just need to do:
- In line 362 change bash to sh.
- In line 424 just before the while add a line saying daemon(0,1); (man daemon for details).
- In line 517 delete "use_sin =" at the beginning of the line.
Step 6: Copy and Run
Now you just need to move the file into the router. We will copy our nk-mips to the /tmp/ directory. This folder always have write permissions and usually also execution permissions. As we've enabled ssh, we can copy the file using scp and execute it remotely using ssh.scp nk-mips root@router-ip:/tmp
ssh root@router-ip "/tmp/nk-mips -shell -s T,5001
Step 7: Disable SSH Access
Now that your remote shell is running you can disable SSH access in the control panel and log into the router just Netcatting to port 5001nc router-ip 5001
CONCLUSION
This was a pretty simple example to demonstrate how to run your own SW on your home router. From here you can explore how to deploy more complex tools that depends on external libraries, how to get your applications installed in the router so they can be re-launched after a reboot... Lots of fun!
How to install Backdoor on Router
![How to install Backdoor on Router]() Reviewed by Unknown
on
10:24 PM
Rating:
Reviewed by Unknown
on
10:24 PM
Rating:




Hello, very interesting the article I am very interested in the subject, but I do not know what to download for my router. My router is a Ubiquiti NanoStation M2 AirOS 6.1.7 firmware. These are some properties when I use the commands by ssh:
ReplyDeletesystem type: Atheros AR7240 (Python)
processor: 0
cpu model: MIPS 24Kc V7.4
BogoMIPS: 259.07
wait instruction: yes
microsecond timers: yes
tlb_entries: 16
extra interrupt vector: yes
watchpoint hardware: yes, count: 4, address / irw mask: [0x0000, 0x0ff8, 0x0ff8, 0x07f8]
ASEs implemented: mips16
shadow register sets: 1
core: 0
VCED exceptions: not available
VCEI exceptions: not available
Please, it would be very helpful if you could help me with information about what I have to do. My email is brianrp2015@gmail.com please contact me as soon as you can. Thanks for everything.
Excelente artigo. Muito interessante de ler. Eu realmente amo ler um artigo tão bom. Obrigado! continue arrasando. aplicativos espiões
ReplyDeleteHow To Install Backdoor On Router - Hacking Trick >>>>> Download Now
ReplyDelete>>>>> Download Full
How To Install Backdoor On Router - Hacking Trick >>>>> Download LINK
>>>>> Download Now
How To Install Backdoor On Router - Hacking Trick >>>>> Download Full
>>>>> Download LINK